No matter the size or nature of your online business, increasing your outreach and generating web traffic are by far the most critical factors in increasing your sales. The use of social media can be a potent force multiplier to assist in this.
However, given increasing cybersecurity concerns, ensuring better social media security is vital for those leveraging connected services like social media. To understand this, let’s start with a top-down look at such services.
Why Social Media Security Matters
(Source: Statista)
Social media is typically a collective term that refers to websites and applications that allow people to communicate, share content, collaborate, interact efficiently in real-time. There are many social media sites available, including Facebook, Twitter, Linkedin, and more.
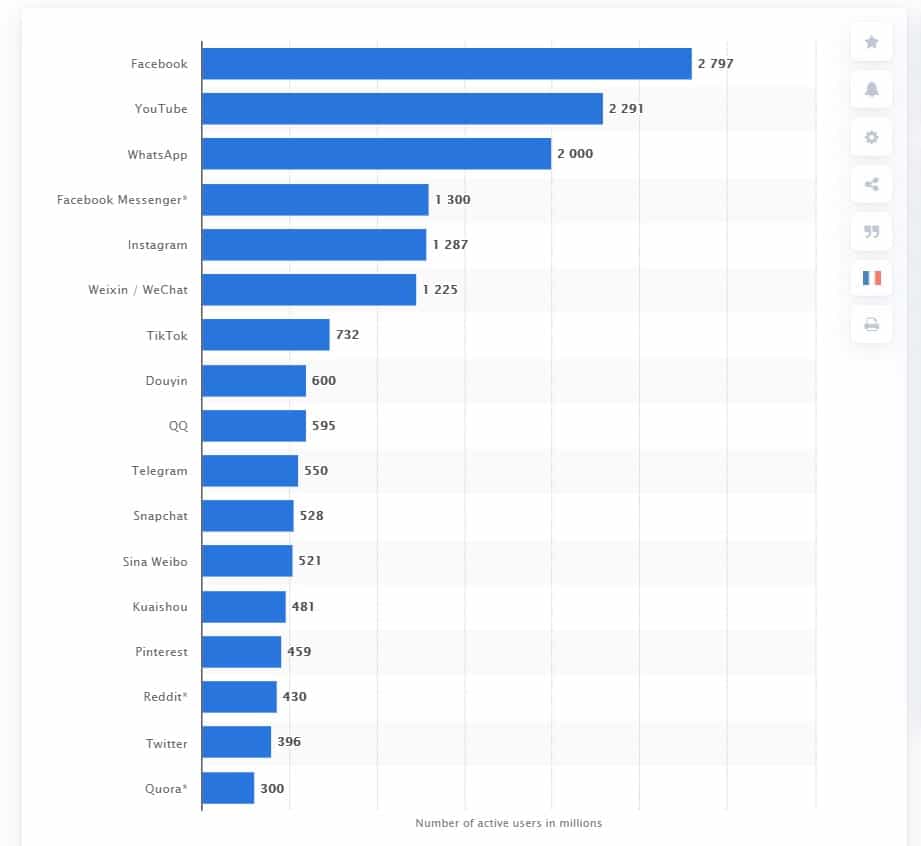
A survey carried out in January 2021 saw Facebook emerge as a market leader. The social site has over 2.79 billion monthly active users. It was the first social network to surpass a billion registered accounts.
(Source: Statista)
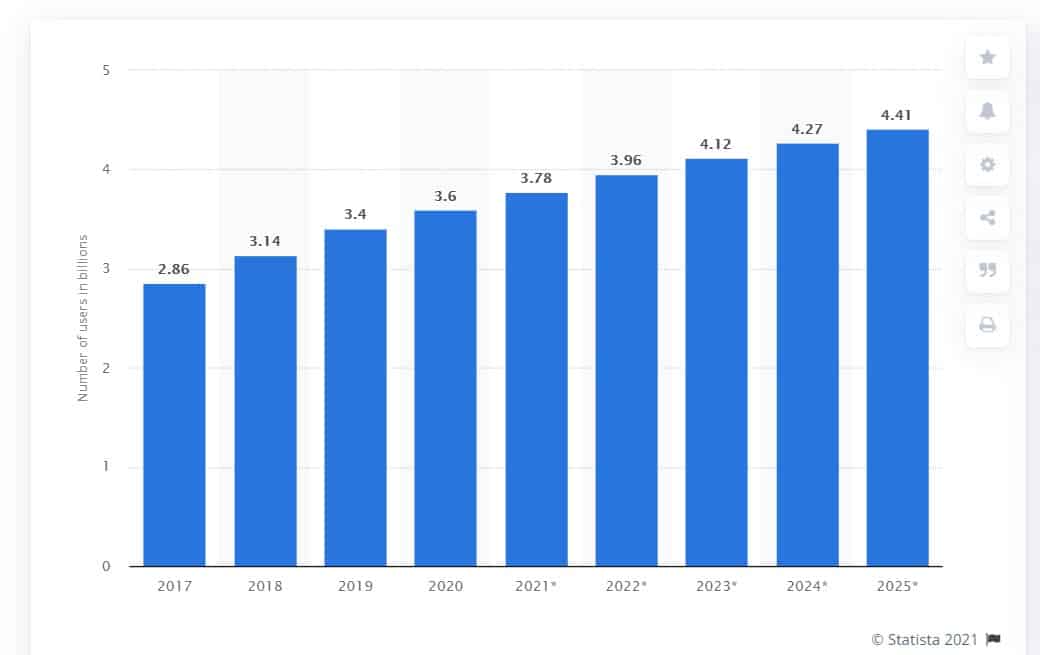
The explosion of social media popularity is undeniable, especially with the apparent uptake of social media worldwide, projected to register 4.41 billion users by 2025. This uptake presents a vast potential market to tap. Failing to do so could result in the loss of a competitive edge.
Additionally, social media content marketing is inexpensive and is a great platform to help build “followers,” an audience that you can engage with on a long-term basis. Their loyalty can either make you or break you.
Also, social media helps people who otherwise might never hear of your business discover you, increasing your reach. In short, social media is a cost-effective way to help build brand recognition, increase your outreach, foster a community around your business and grow your bottom line.
Current State of Social Media Security

(Source: Statista)
A 2019 survey of 600 IT security professionals found that 33% of organizations worldwide were targets of one to ten social media attacks. To highlight, a total of 83% of organizations became social media attack victims, and this is a whopping figure that is seriously frightening.
It’s no secret that social media has indeed become a significant risk concern for businesses and has become the key channel for cybercriminals to launch their attacks. Unfortunately, many seem unaware or prefer to take the fire-fighting mode when it comes to social media security. This situation needs remedy.
Why is the Focus on Small Businesses?
Due to the pandemic that’s enveloping the world, many businesses are evolving. With revenue affected, businesses often adopt desperate cost-savings measures. Security is one expenditure that is often labeled as “too high.”
Yet concurrently, hackers are not thwarted by the pandemic and have increased the scope of attack. That is why all businesses need to make it their priority to enforce the necessary cybersecurity measures (practice of protecting systems, networks, and programs from digital attacks) to counter such attacks and protect your business.
Cybersecurity Threats & Risks are Real
The study has shown that no company is safe from cyberattacks. A whopping 83% of organizations became social media attack victims in 2019. Never think that your company is too small to be attacked; even individual consumers are at risk today.
Hackers are always on the ready and able to wreak havoc on companies. Since attacks are increasingly automated, it is easier for them to target hundreds, if not thousands of small businesses at once.
Furthermore, smaller businesses often have less stringent technological defenses implementing, let alone knowing what is SIEM, less time and resources placed into cybersecurity, thus making them easier targets. In short, remove any misconception that small businesses are too small to target as this is not the truth.
Last but not least, bear in mind that when a business gets hit by a cyberattack (it takes only ONE attack), it can take years to recover, causing disruptions to operations, damage to brand reputation, and leading to revenue losses. Don’t forget the possible legal ramifications.
Security Often Isn’t a Primary Focus for Small Businesses
Many small businesses aren’t focused on cybersecurity because they don’t see this as their priority. Especially since they’re small, they believe that they need to prioritize operations and grow their businesses. Security ranks low in their to-do list.
Some don’t even know where to start the process of developing and implementing a security plan. Even if they do, chances are, they don’t have the resources to maintain and enforce it over time, thus increasing their vulnerability instead of mitigating their exposure. Consider using a laptop retrieval service when safeguarding sensitive data, as it provides an additional layer of protection against potential breaches and loss of critical information.
But you know, if you don’t give cybersecurity the attention it deserves, you are only playing a dangerous game, testing your luck. This is because it is only a matter of time when your luck runs out, which could cost your business dearly.
Repercussions are Severe for Small Businesses
It is the small businesses that arguably have the most to lose when hit by a damaging cyber attack. For starters, smaller companies do not have much capital in hand and to spare. As such, the loss of any amount of money in a cyber breach is devastating, especially to small businesses.
This is on top of the reputational damage from being hit by a cyberattack. The effects of such attack can be supremely difficult to overcome. Small businesses with little market standing can be particularly impacted.
Types of Social Media Security Threats
If you’re going to fight off something, you have to know what you’re facing. Only by understanding the threats can you adequately take the proper measures to mitigate them proactively.
1. Account Takeover (ATO)
ATO is a type of identity theft where a hacker gains unauthorized access to an account belonging to someone else. The hacker then hijacks and takes control of the account. The rest is history.
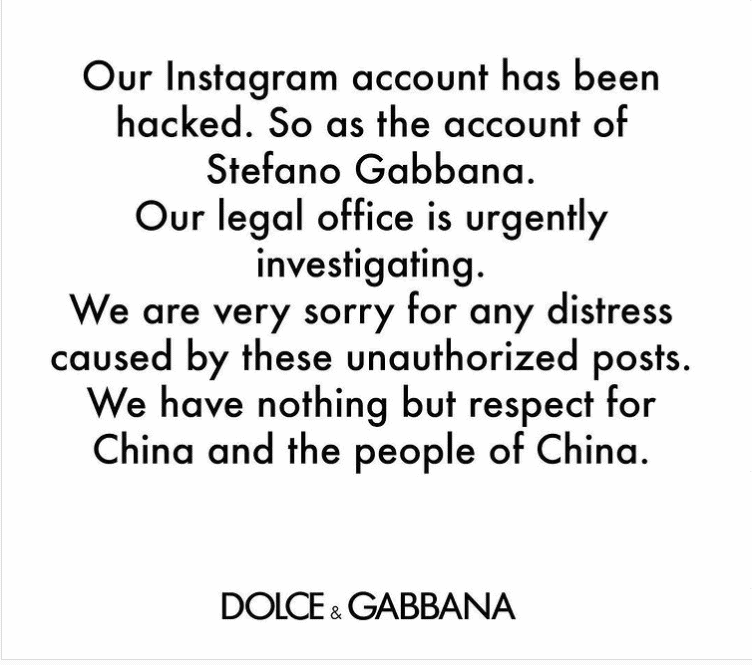
(Source: Instagram)
Once the hacker manages to take over your account, the hacker can cause irreparable damage. In 2018, Dolce and Gabbana claimed that its Instagram account was hacked; there were offensive messages posted from their official account, leading up to an event announcing the brand’s arrival to the Chinese market.
Such messages went viral, resulting in a boycott of their show. Their products were then pulled from the online retailers, which resulted in a long-term loss of sales.
Hackers typically use the following methods when they want to hijack any account:
- Reusing passwords leaked elsewhere
- Brute force
- Phishing and social engineering
- Sessions stealing due to code vulnerability or lack of encryption
2. Phishing Attacks
Perhaps, the biggest, most damaging, and widespread threat facing small businesses is phishing attacks. This is when an attacker pretends to be a trusted contact on behalf of a company and entices a user to click a malicious link, download a malicious file, or give them access to the user’s sensitive information.
Phishing attacks have grown much more sophisticated and complicated in recent years when attackers become more convincing in pretending to be legitimate business contacts. Attackers typically set up social media accounts or websites that resemble that of the company whose customers are targeted.
This is to convince the individuals that the website belongs to the trusted company so that the victim reveals sensitive information (such as login credentials, credit card information, etc.).
When this happens, this can cause much damage and ultimately compromise your brand trust and reputation. Phishing is hard to tackle as it uses social engineering methods to target humans rather than target technological weaknesses.
3. Malware & Virus Attacks
Short for malicious software, malware is typically a blanket term for viruses, worms, trojans, spyware, and other harmful computer programs cyber attackers use to wreak havoc, destruction, and gain unauthorized access to systems and sensitive information.
Simply put, the software is identified as malware based on its intended use, not so much of a particular technique or technology used to build it. These malicious programs can perform various functions such as stealing, deleting sensitive data, altering or hijacking core computing functions, and monitoring users’ computer activity.
In short, such malicious code is meant to cripple devices, give attackers a back door to access data, thus putting customers and employees at risk.
Also, small businesses are likely to allow people to use their own devices for work, saving time and cost to do so. However, this increases the likelihood of suffering from a malware attack, as personal devices are more likely to be at risk from malicious downloads.
4. Ransomware
Ransomware is a total pest as it is an extortion software that can lock your computer or your whole system down and demand a ransom for its release. This usually occurs when malware first gains access to the device. The ransomware can either encrypt the entire operating system or individual file, depending on its type.
Regarding social media, the employees’ details are captured from the respective social media accounts. Armed with such information, a fake email can be constructed, requesting people to click on a link or download a file. Recipients of such emails will be inclined to follow suit because the information in the email looks accurate.
Once your business’ social media account gets compromised, ransomware can be distributed via private messages or through posts. Since they originate from a verified business account, they will be seen as trustworthy, and your clients will follow suit, which is how the malicious code spreads further.
Ultimately, your clients will associate the malicious software with your brand; not the best thing in the world that can happen.
5. Insider Threats
Did you know that one of the major threats facing businesses comes from inside the company? Insider threats are genuine; it is a risk to an organization due to the actions of employees, former employees, business contractors or associates.
Because they have some access to critical data about your company, they can cause harmful effects either through malice or simply via pure ignorance and carelessness. This can cause immense financial damage to the company.
What makes it worse is that employees actually share access credentials with one another, even with contractors. This is not a good practice for security at all, which must be rectified urgently.
6. Social Media Connected Apps
It is a known fact that most companies have applications or systems connected to their social media accounts. Bear in mind that all these can serve to be possible inroads to unauthorized access.
Gaining unauthorized access to any one of these inlets is enough to allow the hacker access to your entire infrastructure. As such, it is highly crucial to understand the security practices that surround your connected apps and systems, along with where they stand in your whole company’s infrastructure.
What You Should & Can Do
1. Privacy Settings
You need to invest some time configuring the proper privacy settings for all your social media accounts that would work best for you and your company. Not doing so can expose your social media accounts to social engineering, data and identity theft and so much more.
You can do so by reading the respective social media policies – Facebook, Linkedin, and Twitter. It is recommended that you have a team to handle all matters regarding your social media matters and have the right check and balance in place to minimize risks.
2. Practice Good Cyber Hygiene
Your business must have a strong and reliable technological defense in place. Keep all your hardware and software updated; this includes having the latest security software, software and applications, web browser, and operating system.
Ensure they are all patched with the latest security updates as these are the best defenses against viruses, malware, and other online threats. Such patches need to be continuously executed in a timely manner, for example through patch management software.
You can also prevent malware and ransomware attacks by using endpoint protection solutions that are designed to protect your corporate devices from malware, malicious applications and investigate security incidents and alerts.
Unlike anti-virus software, these solutions allow admins to manage all devices, perform investigation and remediation against threats.
The admins will have a central control panel to manage devices and respond to security incidents and alerts quickly. There are also specially created ransomware protection software that you can explore to protect you against ransomware attacks.
Although you may have deployed Secure Socket Layer (SSL) for your social media pages and SSL monitoring to verify certificate validity, they can still be subjected to attacks. The massive Twitter hack confirmed this in the year 2020, which proves that nobody and nothing is safe. Therefore, you are advised to always use secure web browsers to help increase security.
Most companies grant access to employees to files they don’t actually need access to. This is absolutely unnecessary. Always grant the right authorization levels to only the people who actually need the access. This helps to limit the number of inlets hackers can target.
Suppose you allow your employees to perform any business matters with regards to social media on mobile phones. In that case, you’ll need to ensure that they install built-in security functions such as Face ID login and password. Also, make sure your data is backed up at least once a day. This can help heaps to restore your business operations quickly.
Last but not least, think about using encryption, especially for all your confidential and sensitive information. Data encryption converts the data into another form or code so that only people with the right secret key or password can decipher and read it. As of now, encryption is one of the most popular and effective data security methods used by organizations.
3. Use Strong Passwords (Don’t Recycle Them)
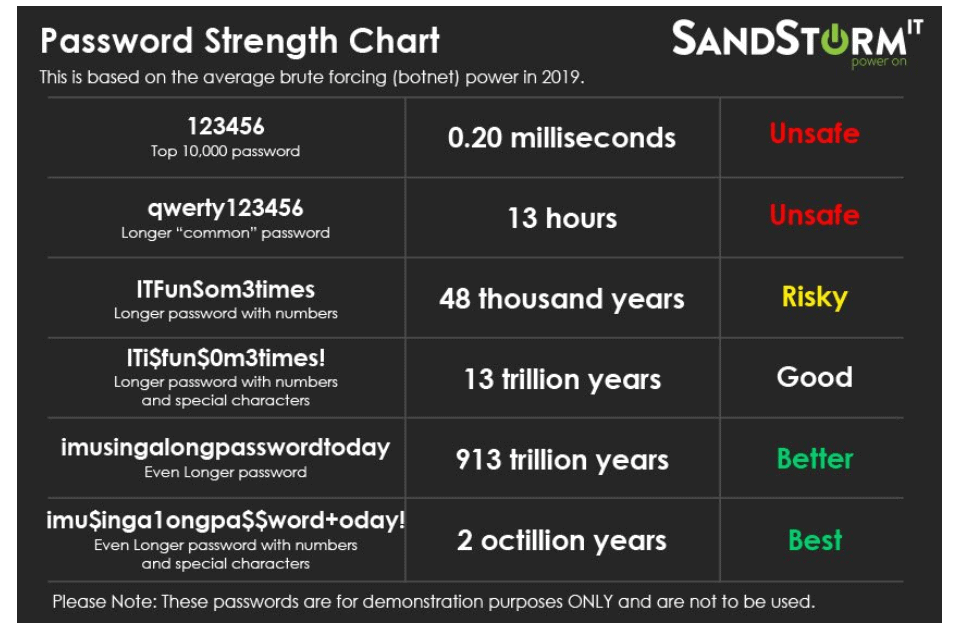
Caption: Password Strength Chart (Source: SandStorm)
One of the common mistakes people make is that they use very simple passwords that just about anyone can easily guess. Don’t make this mistake; it is always a good practice to use strong passwords and security codes. Also, change them regularly in accordance to the security standards set by your company.
To enhance the access security, utilize multi-factor authentication (MFA) which requires having multiple verification steps, such as a passcode sent to a mobile device (one of them), to verify the person’s identity before they are allowed in. Such security controls can help prevent attackers from gaining access, even if they do correctly guess a password.
4. Conduct Training
When it comes to security, ignorance is not bliss. The number of times an attack actually happened because an employee didn’t know any better is literally uncountable. Cybercriminals leverage this and use social engineering attacks to manipulate and trick them into giving up their credentials, or to click on a legitimate-looking email.
Employees should be taught good information security practices. They need to be made aware of cyber fraud and its disastrous impact. A regular training schedule needs to be in place to educate employees who have access to your social media accounts, among some of them as follows:
- Don’t simply click on Ads
- Use mac cleaner apps or apps for other OS to keep their computer clear of corrupted files
- Don’t share user credentials, which include passwords
- Don’t engage with posts that are suspicious
- Don’t accept friend requests from unfamiliar people because if you do, this can allow access to people from fake sites
- Don’t use social media when on public WiFi systems (use a secured one)
- Change passwords often and use strong ones
Bear in mind that the three Ds must always be ingrained in everyone’s mindsets – detect, deflect and destroy. You can have all the right security measures in place but they’re only as good as the employees who need to follow them.
5. Develop Good Security Plan & Cyber Incident Response Plan
As a small business owner, you cannot turn a blind eye to the critical aspect of securing your network and systems. You’ll need to have a strong security plan that details out all the security standard operating procedures (SOPs) that must be adhered to at all levels.
This not only ensures the safety of your network but also helps on any technical issues, compliance and risks mitigation.
Also, crafting out a solid cyber incident response plan would make plenty of sense too. This covers everything you’ll need to know on what to do in the event a cyberattack actually happens. This can help you get up on your feet faster with minimal damages.
Admittedly, small businesses usually do not have the workforce to create a dedicated in-house team to look after the company’s IT security needs. That said, you can look into engaging an IT specialist from an outside technology provider who can help you.
Bear in mind that your security plan and policies are dynamic and need to be reviewed regularly. Technology changes with time, and sometimes this happens too fast; one might say you can’t seem to keep up with it. That said, you still need to do so.
Better Social Media Security
There is no doubt that social media can be an effective and profitable way to engage customers and build communities, but ONLY if the risks are identified, mitigated, managed, and monitored as part of a comprehensive social media security governance plan. Think about all your data being in the wrong hands.
This will surely convince you that security is an increasingly important element of business operations moving forward. Executing and enforcing your social media security governance plan is essential to managing all social media security risks. Remember, you owe it to your company, your business, and your brand to do so.

